Solving the Lo-Fi Tryhackme Room with ChatGPT
Artificial Intelligence is changing the way we solve Capture the Flag (CTF) challenges. Rather than digging through countless security blogs or manuals, we can pose our problems directly to an AI and watch the solution unfold. Here’s a brief story of how I used ChatGPT to crack the “Lo-Fi” room on TryHackMe.
Please note that Lo-Fi is an easy room and also that I was using ChatGPT o1
Enjoy the short write up!
1. Initial Question
After opening a new chat with ChatGPT we must read the room task carefully to craft a useful prompt.
From reading the task I knew the challenge was about LFI/Path Traversal so my first prompt was:
“I’m in a CTF room, and they gave me a website link. The CTF is about LFI / Path traversal. Tell me how to approach this?”
ChatGPT response was (Summary):
- Explained Local File Inclusion (LFI) basics.
- Suggested testing common parameters like page, file, or template.
- Recommended trying path traversal with something like ../../../../etc/passwd%00 .
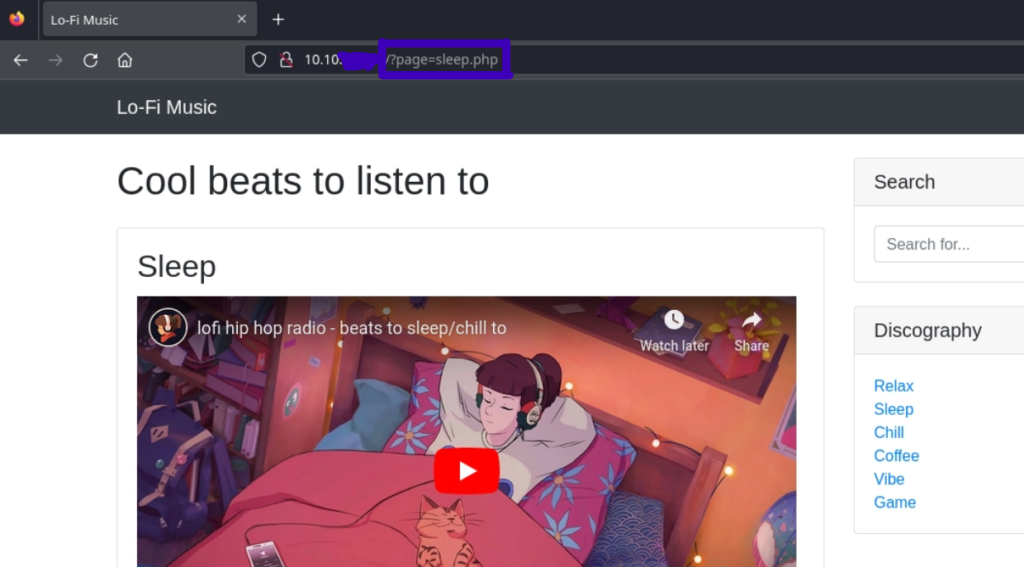
After observing the site I found the page parameter, and since ChatGPT suggested this payload in the summary of the first prompt: http://MACHINE_IP/?page=../../../../etc/passwd%00
2. Testing and Discovery
Next, I told ChatGPT how I tried this specific payload:
“I tried http://MACHINE_IP/?page=../../../../etc/passwd%00 and it gave me the full password file”
ChatGPT response was (Summary):
1. Confirmed we had reading access (LFI vulnerability confirmed!).
2. Suggested searching for a flag file in typical paths (/flag.txt, /root/flag.txt, etc.).
3. Recommended consistent use of the same traversal depth (../../../../) used for /etc/passwd.
3. Finding the Flag
Since the task mentioned the flag is at the root of the file system:

My final prompt was:
“The CTF is telling me the flag is at the root of the filesystem”
So ChatGPT response was (Summary):
1. Advised systematically checking common filenames (flag.txt, root.txt).
2. Suggested reading specific config files if the direct guess didn’t work.
3. Recommended trying http://MACHINE_IP/?page=../../../../flag.txt, which led me right to the flag.
4. Tips for Asking AI to Help Solve CTF Challenges
| Tip | Information |
| Provide Context | AI responses improve significantly when you describe the challenge, environment, and your progress so far. |
| Share Exact Errors or Outputs | Sharing detailed error messages or partial successes (like seeing /etc/passwd) helps the AI adjust its strategy. |
| Ask for Step-by-Step Explanations | Avoiding a single “magic command” fosters learning and deeper understanding of the exploit process. |
| Iterate & Refine | If the first suggestion doesn’t work, mention the error or unexpected result. AI can provide alternative approaches. |
| Keep Security Fundamentals in Mind | AI can help, but do remember your basics, and keep learning. |
Don’t forget to follow us on LinkedIn or Twitter to receive new write-up notifications and if you want to share this post:
Happy Hacking!

